Sandworm, an Inspiration for Hostile Actors

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz.
Sandworm, an Inspiration for Hostile Actors
The Russian military intelligence hacking unit Sandworm presents a cyber proliferation risk with its more sensational operations potentially inspiring or acting as a rough blueprint for other actors, Google’s Mandiant unit has warned.
Google’s Mandiant recently released a report examining Sandworm, perhaps the world’s most notorious state-sponsored group. The report is a useful primer on the most significant Russian cyber activities associated with the country’s invasion of Ukraine.
Sandworm, which Mandiant has now dubbed APT44, has been around since 2009, and the U.S. and U.K. governments formally attribute the group to Unit 74455 of the GRU, Russian military intelligence.
The unit is infamous for launching multiple destructive attacks, including operations against Ukraine’s electricity grid in 2014 and 2015 and the NotPetya attack in 2017.
The report focuses on Sandworm’s activities from 2022, particularly its involvement in the war in Ukraine, as its pre-2022 history has been well covered elsewhere.
For those readers interested in the military application of cyber operations to conventional warfare, the report charts the evolution of Sandworm’s operations throughout the war.
The report describes six phases of Sandworm activity. These range from pre-positioning prior to Russia’s ground invasion, multiple phases focused on disruption, and more recently a refocus toward cyber espionage.
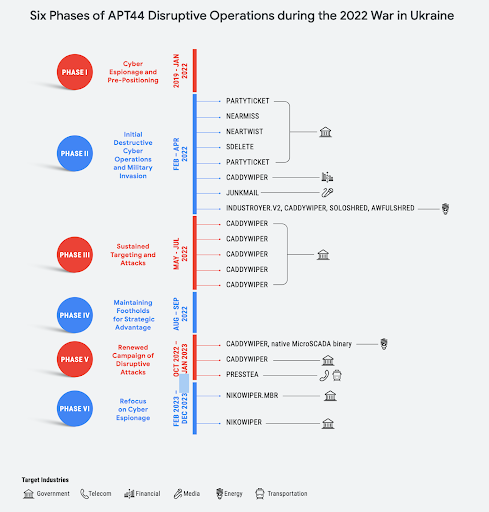
Sandworm aka APT44 disruptive operations in Ukraine.
Since April 2023, Mandiant has seen an increase in direct tactical support to Russia’s military. Sandworm efforts include provisioning infrastructure for Russian forces to extract Telegram and Signal messages from mobile devices captured on the battlefield, and targeting the drone supply chain, including manufacturing and logistics.
Mandiant has also observed a recent increase in targeting of internet service providers and telecommunication companies for espionage and destructive purposes.
The report suggests Sandworm has been under pressure to perform during the war and has looked for support from Russia’s cybercriminals.
We have observed a relative increase in APT44’s use of tools and bulletproof hosting infrastructure acquired from criminal marketplaces. We assess that APT44 has likely long viewed criminally sourced tools and infrastructure as a latent pool of disposable capabilities that can be operationalized on short notice without immediate attributive links to its past operations.
When it comes to information operations, Mandiant believes Sandworm uses a series of front personas to push narratives favorable to Russia, generate perceptions of popular support for the war, and make the GRU’s cyber capabilities appear more potent with exaggerated claims of impact. These personas include XakNet Team, CyberArmyofRussia_Reborn, and Solntsepek.
Mandiant says that “the exact relationship and control over each of these front personas likely varies. However, we have observed the closest operational relationship between APT44 [Sandworm] and CyberArmyofRussia_Reborn.”
Worryingly, CyberArmyofRussia_Reborn recently claimed responsibility for hacking U.S. and European critical infrastructure. As reported in Wired, the apparent victims “include multiple U.S. water utilities in Texas, one Polish wastewater treatment plant, and, reportedly, a French water mill, which the hackers claimed was a French hydroelectric dam.”
Sandworm also regularly uses “living off the land” techniques (abusing legitimate tools already present on networks to carry out its missions). Volt Typhoon, a group linked to the People’s Republic of China, is also using these tactics while attempting to compromise U.S. critical infrastructure for potential sabotage operations. Cybersecurity organizations need to adapt to cope.
Section 702 Amendments Demonstrates Democracy at Work
Late last week, U.S. lawmakers reauthorized Section 702 of the Foreign Intelligence Surveillance Act (FISA) for another two years. Section 702 is the section of FISA that enables U.S. intelligence agencies to compel service providers to help conduct targeted surveillance of foreigners outside the United States.
Its renewal has been controversial because, even though it is targeted at foreigners overseas, Americans’ communications are occasionally swept up into the Section 702 system and the collection occurs on U.S. soil.
In a twist, when much of the prior debate focused on whether to restrict 702 by requiring warrants for searches for U.S. persons, the legislation that passed is being framed by critics as a troubling new expansion of surveillance power.
The reauthorization includes an amendment that expands the definition of “electronic communications service providers” compelled to assist with Section 702 collection.
Privacy advocates argue this new definition is overly broad and will capture too many U.S. organizations. They argue it could even include “delivery personnel, cleaning contractors, and utility providers” that have access to facilities containing communications equipment.
According to the New York Times, however, the intent here is to capture entities like data centers that were not explicitly covered in the former definition and were ruled “out of bounds” by a 2022 Foreign Intelligence Surveillance Court (FISC) ruling.
The FISC, an oversight court, limited the scope of Section 702 by enforcing a narrow interpretation of electronic communications service providers. Congress, in turn, responded by clarifying in legislation what it intended. The Department of Justice also committed to regularly briefing Congress on any applications of the updated definition.
Rather than an unjustified expansion of the surveillance state, we see this incident as an example of democratic processes at work. An oversight court limited the scope of Section 702 collection, and elected lawmakers voted to amend legislation in response, after receiving assurances that they would be given visibility of how these amendments were being used.
How Law Enforcement Should Hack the Hackers
Law enforcement agencies (LEAs) could be given more resources to put them on an equal footing with military and intelligence agencies in fighting cybercrime, a new paper from the Carnegie Endowment proposes.
The paper examines the increasing use of hacking and technical takedowns by LEAs in actions against cybercriminals.
The authors argue that when it comes to fighting cybercrime, militaries and intelligence agencies are “often best equipped and most agile in cyberspace,” but LEAs can be more appropriate and “most impactful” at times and that states need to move beyond a “military-centric framework.”
Militaries and intelligence agencies aren’t built to fight crime but have the technical expertise to disrupt cybercrime groups and are empowered to operate overseas (but usually not domestically). By contrast, LEAs exist to fight crime, have domestic remits to gather evidence, engage with victims and collaborate with private enterprise, but don’t typically operate abroad and don’t have the requisite cyber capability.
If this situation was represented as a Venn diagram, the two circles would not overlap.
The authors argue that one solution is to provide LEAs with more resources so that they are “coequals [with military or intelligence agencies] in the cyber domain.”
That may make sense for countries where cyber skills aren’t a limiting factor, but for many countries (perhaps those smaller than the U.S.) this approach may result in robbing Peter to pay Paul.
However, the main thrust of the paper is that it is still relatively early days for government-backed disruption of cybercrime networks and that there is still lots of room for improvement.
Governments just aren’t that good at whole-of-government programs that involve private-sector collaboration, but that is what is needed to combat cybercrime more effectively.
The Surprising Geography of Cybercrime
A report released earlier this month examines the world’s “geography of cybercrime” and attempts to answer the question “which countries have the most cybercriminals?” It includes some surprising results.
The authors construct a “cybercrime index” simply by asking experts. Of course, cybercrime is a broad field, so the survey covered types of cyber threats:
- Technical products/services (e.g., malware coding, botnet access, access to compromised systems, tool production).
- Attack and extortion (e.g., DDoS attacks, ransomware).
- Data/identity theft (e.g., hacking, phishing, account compromises, credit card compromises).
- Scams (e.g., advance fee fraud, business email compromise, online auction fraud).
- Cashing out/money laundering (e.g., credit card fraud, money mules, illicit virtual currency platforms).
The authors scored different countries across these categories by asking a selection of experts identified through what seems like a reasonable selection process.
Russia and Ukraine top the index, but it is a surprise to us to see China ranked third. This possibly points to a gap in English-language public reporting on Chinese cybercriminals. The U.S. places fourth but actually tops the ranking for data and identity theft.
There are other unexpected results here, including that the U.K. is the highest scored jurisdiction for cashing out and money laundering.
While the index is not perfect, its value lies in prioritizing law enforcement and capacity building efforts around the world. For example, U.K. authorities should dive deeper into why the nation scored so highly in these damaging metrics and respond accordingly.
Three Reasons to Be Cheerful This Week:
- U.K. laws deter deepfake sites: Two of the biggest explicit deepfake websites have started blocking visits from people in the U.K. The U.K. has committed to introducing laws that make the creation of explicit deepfakes without consent a crime.
- LabHost takedown: An international law enforcement collaboration has taken down the LabHost Phishing-as-a-Service platform. Our favorite part is that the U.K.’s Metropolitan Police sent 800 Labhost users a message “telling them we know who they are and what they’ve been doing.” Risky Business News has more coverage.
- Intruders are getting caught faster: Mandiant’s M-Trends 2024 report says that half of all intrusions are now identified within 10 days, an all-time low, and that a whopping 43 percent of all incidents last year were detected in one week or less. Long dwell times are also a rarity, and only 6 percent of 2023 intrusions went undetected for more than a year.
Shorts
Visa Restrictions on Spyware Villains
The U.S. Department of State announced it was imposing visa restrictions “on 13 individuals who have been involved in the development and sale of commercial spyware or who are immediate family members of those involved.”
The U.S. government explicitly linked these restrictions to human rights abuses and announced them in conjunction with the release of the 2023 edition of the State Department’s annual Human Rights Report.
In remarks at the launch of the report, Secretary of State Antony Blinken said the restrictions were applied to “more than a dozen individuals who contributed to human rights abuses by helping to develop and sell [commercial spyware].”
This is good because it signals that visa restrictions are part of an ongoing process and not just a one-off phenomenon. Risky Business News has more coverage and reports that the names of the affected individuals won’t be made public for legal reasons. We wonder, however, if some identifying information, such as the company they are associated with, would be useful to deter people.
TikTok Ban Passed
The U.S. Senate has passed a bill that will force TikTok’s Chinese parent company, ByteDance, to divest itself of the company or face a ban in the U.S. President Biden has said he will sign the legislation.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq look at Google’s review of zero-days in 2023. They discuss what this kind of information tells us and how Google’s perspective influences the report.
From Risky Biz News:
FTA hacking spree continues with CrushFTP zero-day: An unidentified threat actor is exploiting a zero-day vulnerability in CrushFTP, an enterprise file-transfer software solution.
CrushFTP released a patch on Friday, hours after it learned of the attacks from the Airbus CERT team. CrowdStrike also confirmed the zero-day later in the day and described the attacks as “targeted.”
The zero-day was assigned CVE-2024-4040.
Just like most of these incidents, there is also some sort of misunderstanding and drama about what exactly is taking place. This stems from two conflicting messages that CrushFTP has put out about the issue.
In private messages sent to customers last week, CrushFTP said the vulnerability allowed unauthenticated attackers to escape the virtual file system and download user files.
In a public changelog, the company said that only authenticated attackers can exploit this.
[more on Risky Business News]
Authorities take down LabHost, one of the world’s largest phishing platforms: Law enforcement agencies from 19 countries have collaborated to take down a cybercrime service named LabHost that provided tools to easily set up and run phishing pages.
The service launched in late 2021 and was what you would call a PhaaS, or Phishing-as-a-Service platform.
According to Trend Micro, it was one of the most sophisticated PhaaS platforms on the market today. Besides the standard features listed above, it could also allow threat actors to create custom phishing pages for any service they wanted to target and came with an SMS phishing (smishing) component named LabSend.
It was also one of the first phishing services to include solid support for bypassing multi-factor authentication by supporting proxy-based AitM (Attacker-in-the-Middle) phishing techniques.
[more on Risky Business News]
DPRK leaky server: A North Korean cloud server was left exposed on the internet last year and leaked animation-related projects. The exposed files suggest that Western animation studios might have inadvertently hired North Korean animators for their projects. According to the leaked files, North Korean animators appear to have worked on shows that have run or will run on the BBC, Amazon Prime, and HBO Max. Titles include the likes of Invincible, Dahliya In Bloom, Octonauts, and Iyanu, Child of Wonder. [Additional coverage in 38North]





