The I-Soon Data Leak + Disruption, Disruption Everywhere

Editor’s Note: This newsletter is part of a collaboration between Lawfare and Risky Business. You can find the full version of the Seriously Risky Business newsletter and previous editions on news.risky.biz.
Risky Biz Briefing: The I-Soon Data Leak
An unknown individual or entity has leaked files that suggest a Chinese cybersecurity company is developing malware and carrying out cyber espionage on behalf of the Chinese government.
The data allegedly belongs to I-Soon, a company based in Chengdu that also does business as Sichuan Anxun (四川安洵信息技术有限公司).
I-Soon was already on the radar of some cybersecurity researchers after being sued by a firm from the same city, a company known as Chengdu 404. According to the U.S. Department of Justice, Chengdu 404 is linked to the cyber espionage group known as APT41. There are also matches in the data leak to indicators of compromise from previous cyber espionage campaigns.
A Natto Thoughts report from October 2023 described I-Soon as one of many Chengdu-based cybersecurity companies that work as contractors for the Chinese government, providing the technical know-how and personnel for internal surveillance operations and cyber espionage. Chengdu, according to reports, is a cybersecurity talent and recruitment hub for China’s Ministry of State Security.
What’s in the files?
The original I-Soon leak GitHub repository is here, and a machine-translated version of the files is available in this repo.
The data is only loosely organized. According to threat intelligence analysts who have gone through it, the files include internal chats, business pitches, documentation describing the company’s products, and what appears to be stolen victim data, such as credentials and even CDRs (call detail records) from hacked telecommunications companies. No source code was included.
The business documents include pitches and presentations about the company’s services including “penetration testing,” surveillance operations, and descriptions of its tools.
Business pitches included in the leaked files also show I-Soon’s interest in landing surveillance contracts in China’s Xinjiang province, home of the country’s Uyghur Muslim minority.
The I-Soon data also includes files that appear to be documentation or more technical business pitches that describe products of an extremely broad range of capabilities. These include:
- Malware designed to run on Windows, macOS, Linux, iOS, and Android.
- A platform to collect and analyze email data.
- A platform to hack into Outlook accounts.
- A Twitter monitoring platform.
- A reconnaissance platform using open-source intelligence data.
- Physical hardware devices meant to be used for on-premises hacking, typically targeting WiFi networks.
- Communications equipment using a Tor-like network for agents working abroad.
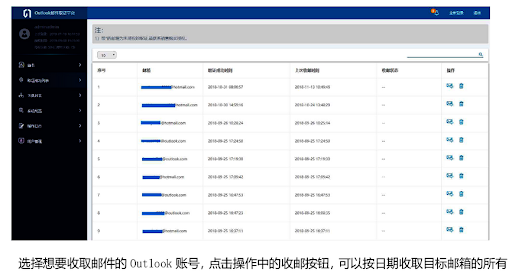
Screenshot of one of the I-Soon tools designed to access Outlook accounts.
There’s a slide deck advertising the company’s “APT Team.” We’re struck by the irony that a term coined within the U.S. Department of Defense to describe Chinese cyber espionage efforts is now used in the marketing materials of the firms actually carrying out said Chinese cyber espionage.
Slide from the I-Soon repository advertising APT services.
What does it tell us?
At one level, this leak does not change anything—it is no secret that China is a prolific cyber espionage actor, so it probably will not change people’s views about the country. However, there are interesting gold nuggets here, and the leak also provides a behind-the-scenes view of China’s espionage activities. There’s a lot of color here.
One of the leaked internal chats references the Tianfu Cup, a local hacking contest set up by Chinese authorities following the format of ZDI’s Pwn2Own.
In these messages, Shutd0wn—the pseudonym of I-Soon CEO Wu Haibo—asked for proof-of-concept code (POC) for exploits used at the Tianfu Cup 2021 edition.
Shutd0wn to lengmo: Regarding the 0-day vulnerabilities in the Tianfu Cup competition, it is said that the POCs were given to the public security bureau. Can we obtain them?
Lengmo to Shutd0wn: We can’t get them. I asked that day, and the department gave them to Jiangsu. [The conversation appears to refer to the Ministry of Public Security, although the Jiangsu branch of the Ministry of State Security makes more sense given its historical activity.]
China’s vulnerability disclosure rules have changed in recent years to funnel vulnerabilities through its intelligence agencies. There is also strong circumstantial evidence that these vulnerabilities have been used in espionage operations.
In May 2021, the MIT Technology Review claimed an exploit showcased at the 2018 Tianfu Cup was used to spy on China’s Uyghur Muslim minority shortly after it was demonstrated at the contest and before a patch was released. And an analysis by threat intelligence firm Recorded Future of how long it took vulnerabilities to be published to China’s national vulnerability database (as compared to publication speed at its U.S. equivalent) also found suggestive patterns. The publication of more severe vulnerabilities (those with a higher CVSS score) and those linked to malware used by Chinese espionage groups was delayed when compared to more run-of-the-mill vulnerabilities. This suggests that the Ministry of State Security is assessing whether vulnerabilities can be exploited before they are revealed.
Assuming these chat messages are legitimate, they confirm that China’s own espionage contractors believe that the government is using its local vulnerability researchers’ discoveries for cyber espionage purposes.
One of the leaked internal chats suggests I-Soon contracts with China’s Ministry of State Security and its Ministry of Public Security—through each agencies’ network of local bureaus.
Other chats provide a window into the ecosystem of contractors and subcontractors providing these specialized cybersecurity services. One suggests the company, along with several other contractors in a highly competitive market, is among the recipients of lists of targets from government agencies.
There is evidence of an interesting “try before you buy” approach to espionage here. In one chat, the first participant is trying to sell data from Jens Stoltenberg, the secretary general of NATO. The other participant replies that “they looked at the sample but are not interested.” The first says that they are “really short of money” and offers to lower their price. But the second person replies that “what you consider valuable may not be considered valuable by others.”
“It’s not about whether it is cheap or not,” the messages continue, “it’s because they don’t think it is worth spending money on.”
Ouch. Sorry, Jens.
The leak includes what look like several target lists that cover a number of governments, including Pakistan, India, Malaysia, Turkey, India, Egypt, France, Cambodia, Indonesia, Vietnam, Myanmar, the Philippines, and Afghanistan, as well as NATO, universities, and the Hong Kong pro-democracy movement.
Dakota Cary, a China-focused consultant at SentinelOne who has published extensively on Chinese cyber actors, told Seriously Risky Business he noticed the “cut-rate prices” the company was paid.
“The leaks show that a company, paid relatively little money and competing for low-value contracts from the state, is responsible for massive online hacking campaigns. If hacking into the Vietnamese government was more difficult, we would expect the company to be paid more than USD$60,000,” he continued.
Although from a narrow cybersecurity perspective the leaks themselves are interesting but not earthshaking, there is still the possibility of diplomatic fallout if an affected government takes offense.
Huong Le Thu, a Southeast Asia expert at the Center for Strategic and International Studies, told Seriously Risky Business that she didn’t think this was likely for most of the Indo-Pacific countries involved.
In the past, these countries had been “very careful” about how they react to prior Chinese intrusions, she said, although in this case she thought the Philippines and perhaps India might be potential exceptions. China has been contesting a Philippine presence in the South China Sea, so it depends “on how escalatory [new President] Marcos Jr wants to be.” In India, the story of the leak could play into the upcoming election “if it suits nationalists moods.”
But this is also an opportunity for U.S. diplomats too, and Le Thu thought that the U.S. would use this to brief countries in the region about Chinese espionage. In the wake of the spy balloon fiasco last year, for example, the U.S. briefed 40 foreign embassies on China’s aerial surveillance program. This seems like a golden opportunity for a set of briefings about Chinese cyber espionage.
This is a lot of fun for those of us who follow Chinese cyber activity closely and provides some fascinating insight into how at least some of the lower tier Chinese espionage contractors work. But it’s not any sort of game changer and will not have the impact that the Edward Snowden leaks had on Five Eyes operations.
Disruption, Disruption Everywhere
There is emerging evidence that the worldwide pace of government-sanctioned cyber disruption is picking up.
Since Dec. 20, 2023, a spate of disruption operations have targeted cybercriminal and nation-state adversaries.
This week, the U.K.’s National Crime Authority announced the takedown of the LockBit ransomware gang. This is covered in depth in Risky Business News and covered briefly in this week’s “Three Reasons to Be Cheerful” section.
Last week, the U.S. Department of Justice announced the court-authorized disruption of a small office/home office router botnet controlled by the GRU (Russian military intelligence). Interestingly, this network leveraged Moobot malware, a Mirai-variant malware associated with a known criminal group that has been around since at least 2019. The GRU then “repurposed the botnet, turning it into a global cyber espionage surveillance platform,” says the Justice Department press release.
At the end of January, the Justice Department announced a similar disruption of the KV botnet, a botnet used by Chinese cyber espionage groups.
And on Dec. 19, 2023, the Justice Department announced it had taken action against the AlphV/BlackCat ransomware gang, which its press release stated was the “second most prolific ransomware-as-a-service variant.”
That’s an unprecedented amount of disruption over the past two months.
Speaking at the Munich Cyber Security Conference, Anne Neuberger, the White House deputy national security adviser for cyber and emerging technologies, said that ransomware takedown operations weren’t occurring frequently enough, as reported in The Record.
“We’re doing that every 8-12 months, but they have to be more frequent,” she said. “We’ve made progress, but there is far more to be done.”
Adversary groups adjust when their operations are interrupted or hampered, but it takes time. We’re hopeful that these recent disruption operations are not just a flash in the pan but instead are the start of a new trend.
Three Reasons to Be Cheerful This Week:
- LockBit’s entire criminal enterprise seized by international law enforcement action: Operation Cronos, led by the U.K.’s National Crime Agency, seized infrastructure, froze cryptocurrency wallets, released keys and decryption tools, arrested members, and imposed sanctions. Particularly pleasing was the excellent trolling of LockBit members and affiliates carried out by Op Cronos. Risky Business News has comprehensive coverage.
- Tech companies sign artificial intelligence (AI) election accord: A coalition of tech companies announced the accord at the Munich Security Conference last week. The Associated Press described the accord as “largely symbolic,” but with a number of significant elections taking place this year, there is no doubt that AI technologies will be used in deceptive ways. Firms that have signed up so far include Microsoft, OpenAI, Amazon, Meta, Stability AI, TikTok, and X, among others.
- Spyware firm Variston bleeding staff: Former employees of Variston, a Barcelona-based spyware maker, told TechCrunch that attention and public reporting from Google’s Threat Analysis Group made life difficult for the startup. This has caused an exodus of staff from the company, and some former employees even say Variston is shutting down.
Shorts
How Threat Actors Use AI
Last week, both Microsoft and OpenAI published reports examining how various cyber threat actors are using AI services such as large language models (LLMs, the technology behind ChatGPT ).
The reports cover an array of state-affiliated threat actors from the usual suspects—Russia, Iran, North Korea, and China. OpenAI’s report summarizes the activity as follows:
These actors generally sought to use OpenAI services for querying open-source information, translating, finding coding errors, and running basic coding tasks.
Specifically:
- Charcoal Typhoon [Ed: China] used our services to research various companies and cybersecurity tools, debug code and generate scripts, and create content likely for use in phishing campaigns.
- Salmon Typhoon [Ed: China] used our services to translate technical papers, retrieve publicly available information on multiple intelligence agencies and regional threat actors, assist with coding, and research common ways processes could be hidden on a system.
- Crimson Sandstorm [Ed: Iran] used our services for scripting support related to app and web development, generating content likely for spear-phishing campaigns, and researching common ways malware could evade detection.
- Emerald Sleet [Ed: North Korea] used our services to identify experts and organisations focused on defense issues in the Asia-Pacific region, understand publicly available vulnerabilities, help with basic scripting tasks, and draft content that could be used in phishing campaigns.
- Forest Blizzard [Ed: Russian] used our services primarily for open-source research into satellite communication protocols and radar imaging technology, as well as for support with scripting tasks.
Both reports describe these activities as either “experimental” or providing only “limited, incremental” advantages over currently available non-AI-powered methods.
In all the cited cases, the accounts associated with these groups have been terminated.
Usernames for Signal
Signal has announced upcoming changes that make phone numbers more private on the app.
These features are currently in beta, but within Signal a user will be able to give out a username instead of a phone number and will be much better able to control who sees their number.
These are definitely privacy-enhancing features, but we wonder about whether this increases the likelihood the service will be used in malicious ways. More coverage in Wired.
Risky Biz Talks
In the latest “Between Two Nerds” discussion, Tom Uren and The Grugq reassess Russian cyber activity in the early days of its invasion of Ukraine.
From Risky Biz News:
New NSO Group capability reproduced after court disclosure: ENEA, a Sweden-based telecommunications security firm, claims it reproduced a user fingerprinting technique advertised and sold by Israeli spyware vendor NSO Group.
Named MMS Fingerprinting, the technique can collect information on a target’s smartphone and operating system just by sending an MMS message.
NSO Group claims no user interaction is needed besides knowing the target’s phone number.
ENEA says that it learned about this technique after reading court documents filed by WhatsApp in 2019 in its lawsuit against NSO Group—with MMS Fingerprinting being mentioned in a contract between an NSO reseller and Ghana’s telecommunications regulator.
[more on Risky Business News]
Microsoft will replace Secure Boot certificates to avoid 2026 boot-pocalypse: Microsoft has released this week an optional servicing update that rotates digital certificates used by the Secure Boot feature.
The update is likely to unclench some sphincters in the information technology administration and cybersecurity community, as the certificates were set to expire in 2026.
Once the certificates expired, Windows systems where Secure Boot was enabled would have failed to boot. The issue would have also impacted some Linux systems that use Microsoft certificates for their bootloader, such as Ubuntu.
[more on Risky Business News]
Pegasus in Poland: Polish Prime Minister Donald Tusk says he has obtained official documentation confirming that the country’s previous government extensively used the Pegasus spyware. Tusk says the former government targeted a “very long” list of targets. The list is much larger than previous reports, and most targets were opposition politicians. Tusk described the hacking campaign as “illegal.” Poland’s previous government was led by the right-wing Law and Justice (PiS) party.
[additional coverage in the Associated Press and Gazeta.pl]



-(1).jpg?sfvrsn=a0f57148_5)


